_
A fully autonomous agentic system, developed to identify, analyze and validate vulnerabilities in APIs.
Cheaper
The fully autonomous approach reduces the need for human intervention, reducing costs.
Faster
Can analyze vulnerabilities non-stop, perfect for large APIs containing hundreds of distinct endpoints.
Superior
The agentic approach uses real‑world exploit paths, for higher accuracy than traditional scanners.
Our Solution
APIs are the backbone of digital systems — and their weakest link when left unguarded. APISamurai is your silent guardian: an intelligent, autonomous agent that relentlessly detects and validates API vulnerabilities before attackers do. No need for manual penetration testing or time-consuming static scans.
A fully autonomous agentic system, developed to identify, analyze and validate vulnerabilities in APIs.
How it works
Documentation
You provide your API description in OpenAPI or Swagger format and access details for a test environment. apiSamurai uses this to understand your endpoints, inputs, and business rules.
Identification & Analysis
Using a set of workflows, apiSamurai performs a deep analysis of your documentation, looking for possible vulnerable endpoints and indicators of weak points: authentication gaps, access control issues, data exposure, and more. These are grouped based on their nature and severity.
Exploitation & Validation
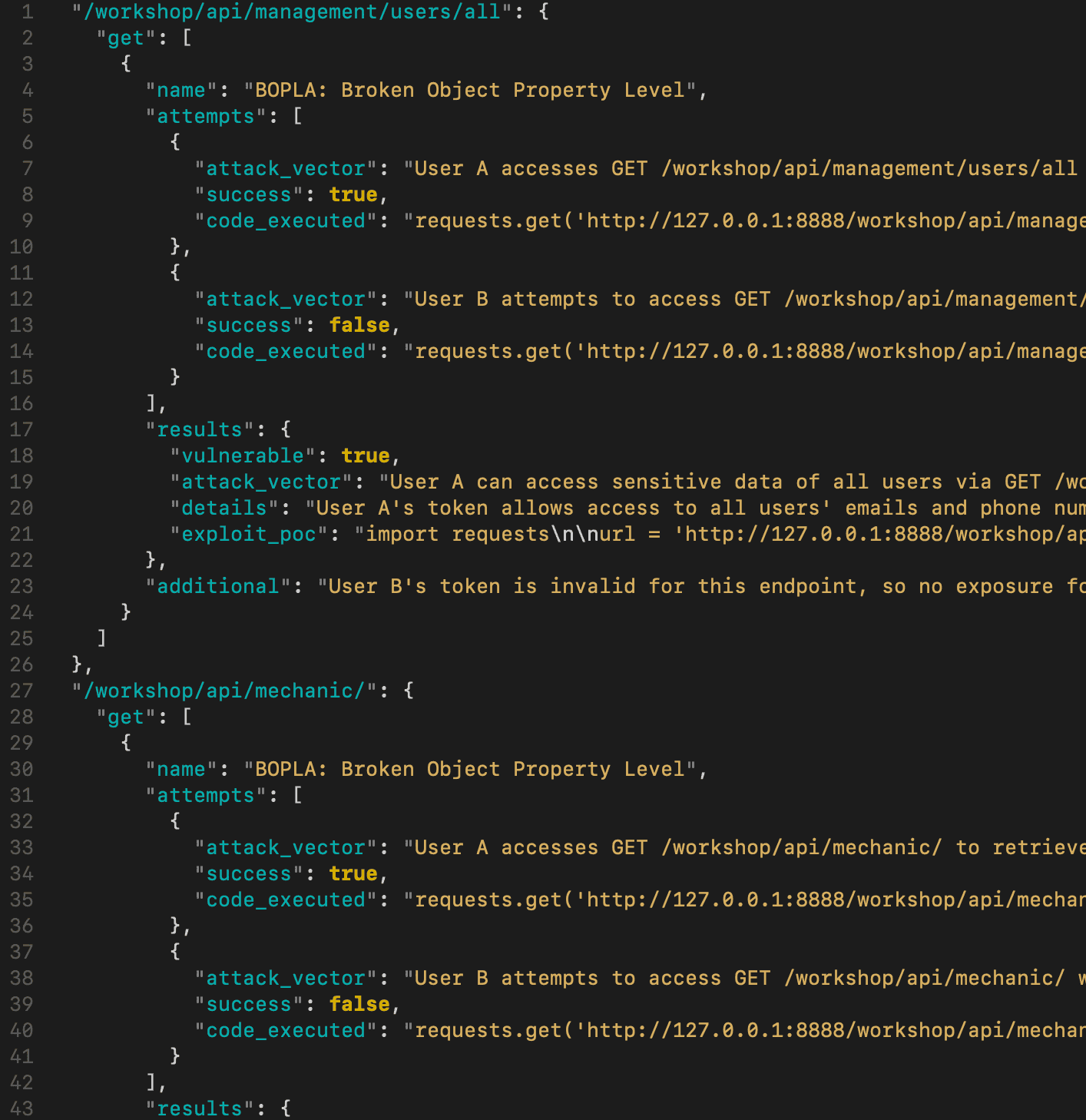
With the help of LLM‑powered agents, apiSamurai exploits identified weak points using test users in a supervised manner, and validates them using real‑world exploit paths for higher accuracy than traditional scanners.
Discovery Report
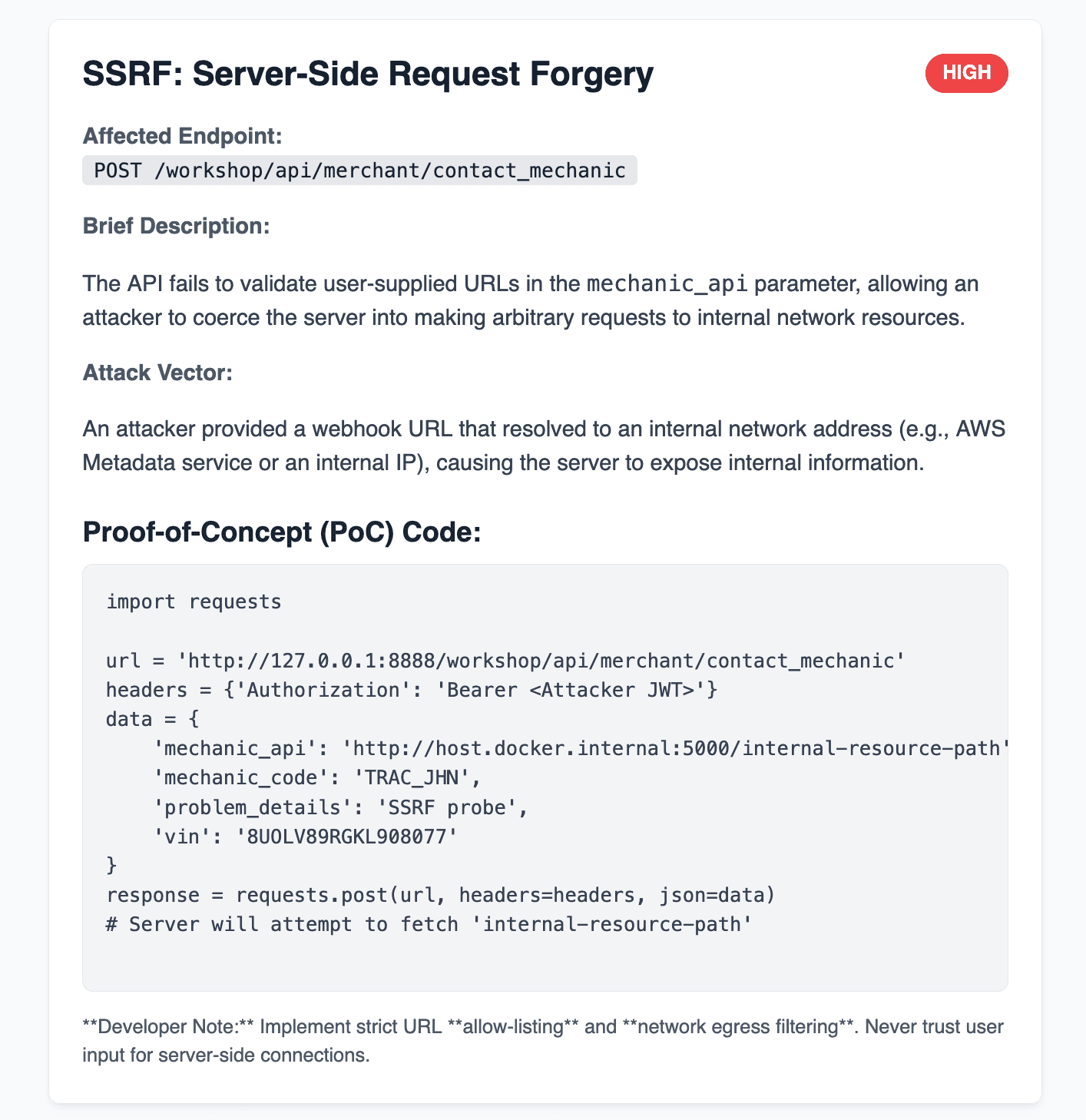
Results are aggregated into a report including vulnerable endpoints, vulnerability categories, descriptions, exploit paths followed by apiSamurai, and proof‑of‑concept code for reproducibility.
Our solution provides comprehensive API vulnerability detection using advanced AI agents that understand your API structure and can identify security flaws that traditional tools miss.
Case study
Results of the vulnerability scan performed to a Napptilus associate:
Endpoints Analyzed
Successfully analyzed and tested against different types of vulnerabilities
Vulnerable Endpoints
Distinct endpoints presented vulnerabilities, mostly being BOLA, BFLA and BOPLA
Critical Vulnerabilities
Of vulnerabilities were classified as critical by the developers due to their potential abuse
Pricing
Want to see how your APIs stack up against potential threats? Submit your details for a free complimentary vulnerability scan. Our team will manually review each request to determine suitability for our free scan service.
Free Scan
Perfect starting point
Get to know the tool and view reports. Manual review and approval process with response within 72 hours.**
Single Scan
One-time comprehensive scan
Unique scan of your API. Team studies your API for accurate pricing. Detailed vulnerability report with proof-of-concept code included.
Periodic Scan
Regular security monitoring
Multiple scans over time with ongoing security monitoring. Customized scanning schedule with trend analysis and reporting.
** The form guides you through the essentials: who you are, contact details, API base URL, access for a couple of test users or keys, and your OpenAPI/Swagger file. After submission, we do a brief manual review and reply within 72 hours. If approved, we run an agentic AI scan and share a clear summary of findings with next steps.
Contact us
Contact us for tailored solutions that promise seamless integration, innovation, and success.